In order to hack on private programs, you must receive invitations to them. You can receive invitations if you meet the following criteria:
- Established reputation
- Non-negative signal
- Clear record with zero code of conduct violations
Again, with the Hackerone markdown example, having the hanging single quote combined with additional html later in the page with a single quote would create vulnerability.
A Hacker's Blog of Unintended Use and Insomnia. At HackerOne’s recent Security@ conference, Slack and Hyatt’s CISOs sat down for a chat about their challenges and the hacks they use to quantify risk. Bug Bounty Playbook Ghostlulz download Z-Library. Download books for free. Cisco offers weather updates for different products released due to the use of standard SSH-keys.
When your Reputation, Signal, and Impact are high enough, you'll join the pool of hackers that receive access to private programs. Once you start receiving invitations to those programs, remember, the one universal rule is to not talk about the private programs you're a part of.
HackerOne manages invitations for programs by:
- Daily checking to see if the program has met their report volume target in the last 30-days
- Inviting hackers for the program if they're not reaching their report volume target
How Invitations Work
The number of invitations HackerOne sends is based on the program's report volume on a rolling 30-day basis. These are the use cases as to how HackerOne sends invitations:
Hacker One Markdown Free
| Case | Action |
|---|---|
| The program is far from meeting their report volume. | HackerOne will gradually increase the number of invitations so the program can meet their report volume. |
| The program is receiving more reports while still being under their report volume. | HackerOne will send out fewer invitations. |
| The program's report volume is met. | Invitations will pause until the volume drops below the target in the 30 day window. |
| The program's report volume is set to 0. | No invitations will be sent. |
Sometimes programs will manually invite you to hack on their programs. Keep in mind that it's a violation of Disclosure Guidelines for you to reach out to a private program in request for an invitation.
Invitation Expirations
Invitations to hack a program expire in 1 week. You may want to reject an invitation for one reason or another. The sooner you let HackerOne know that you're not going to accept the invitation, the sooner the invite can be sent to another hacker.
Hackerone Markdown Xss
Invitation Preferences
Some hackers may want to get invites from any private program, while others only want invites from those offering bounties, and some may not want any invitations at all.
To choose when to receive invitations to private programs, you can navigate to Settings > Invitation Preferences.
You can choose from these options:
| Field | Detail |
|---|---|
| I want to receive invitations to private programs | Select yes to receive invitations from private programs. |
| Pause private program invitations | Select yes to stop receiving invitations from private programs. |
| Pause private program invitations until | Enter the date you want to stop receiving invitations until. |
| Cryptocurrency preferences | Select yes to opt-out from receiving cryptocurrency program invitations. This field is currently in beta |
| Bounty preferences | Select yes to only receive invitations to programs that award a bounty. (Currently in beta) Move the slider to indicate the minimum bounty amount for programs you’d like to receive invitations from. |
Hacker One Markdown Game

Hacker One Markdown 2
Hacker One Markdown Download
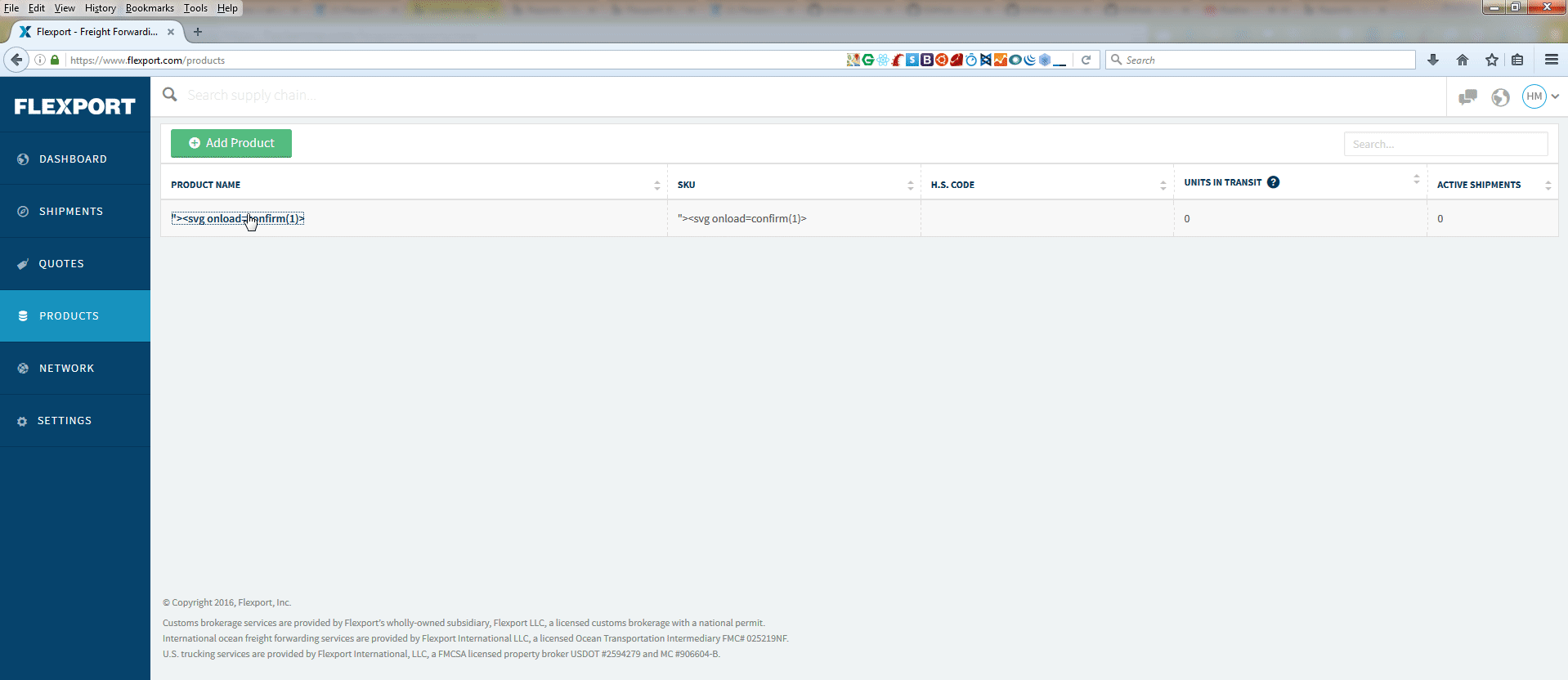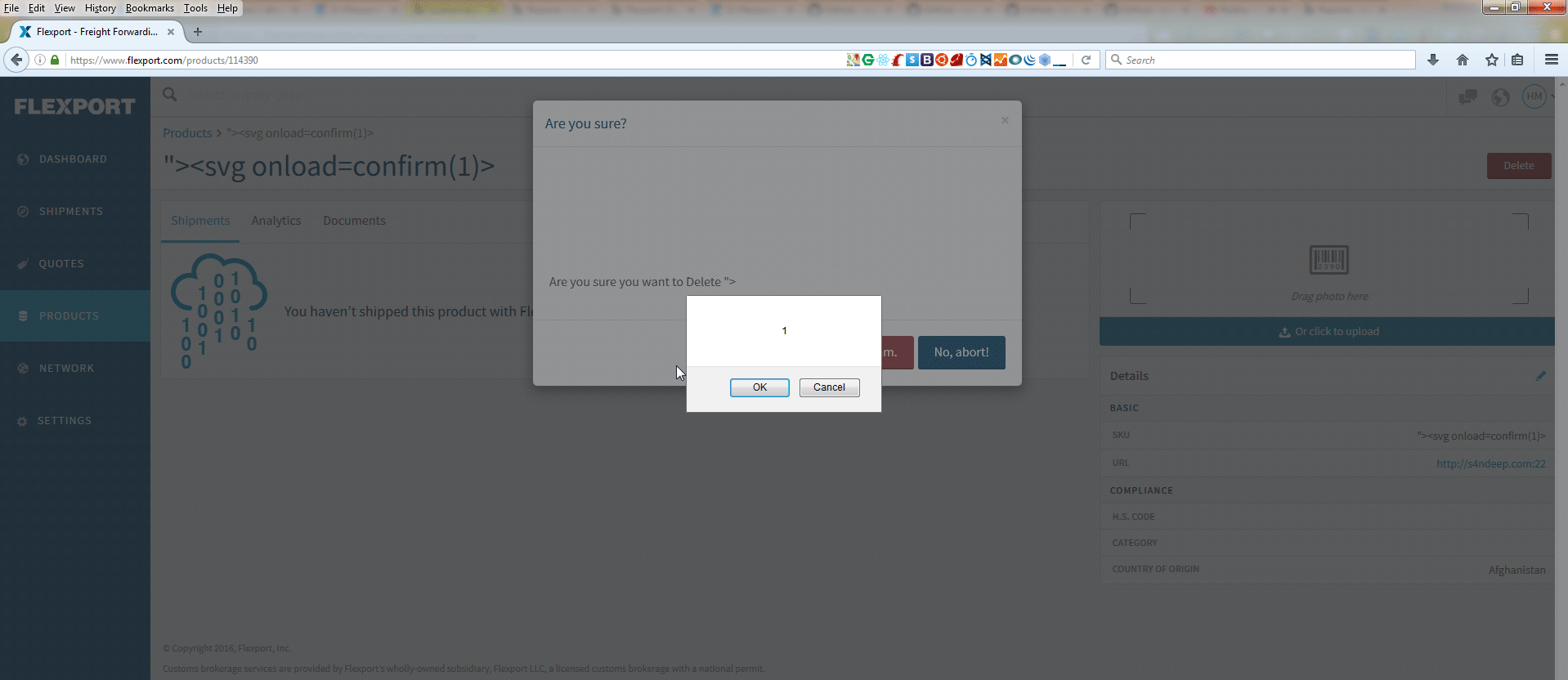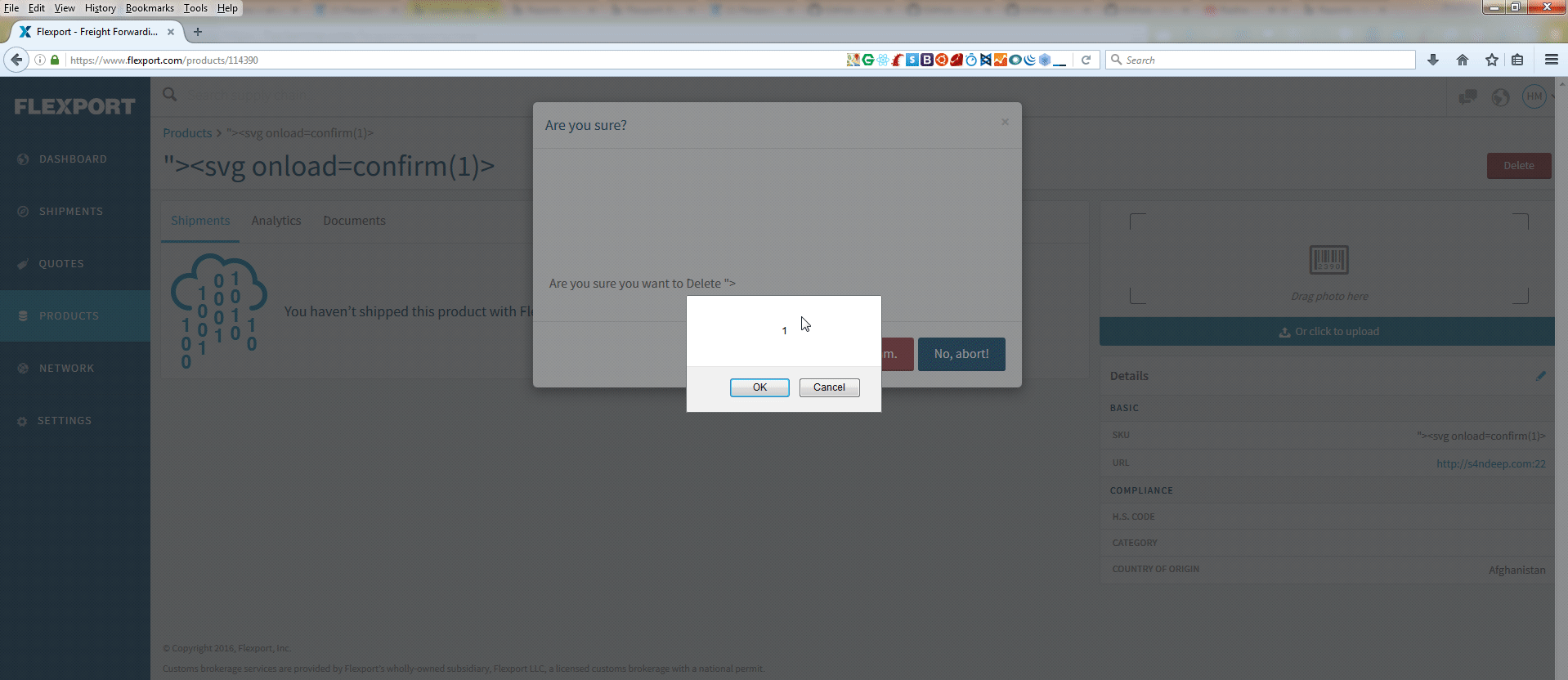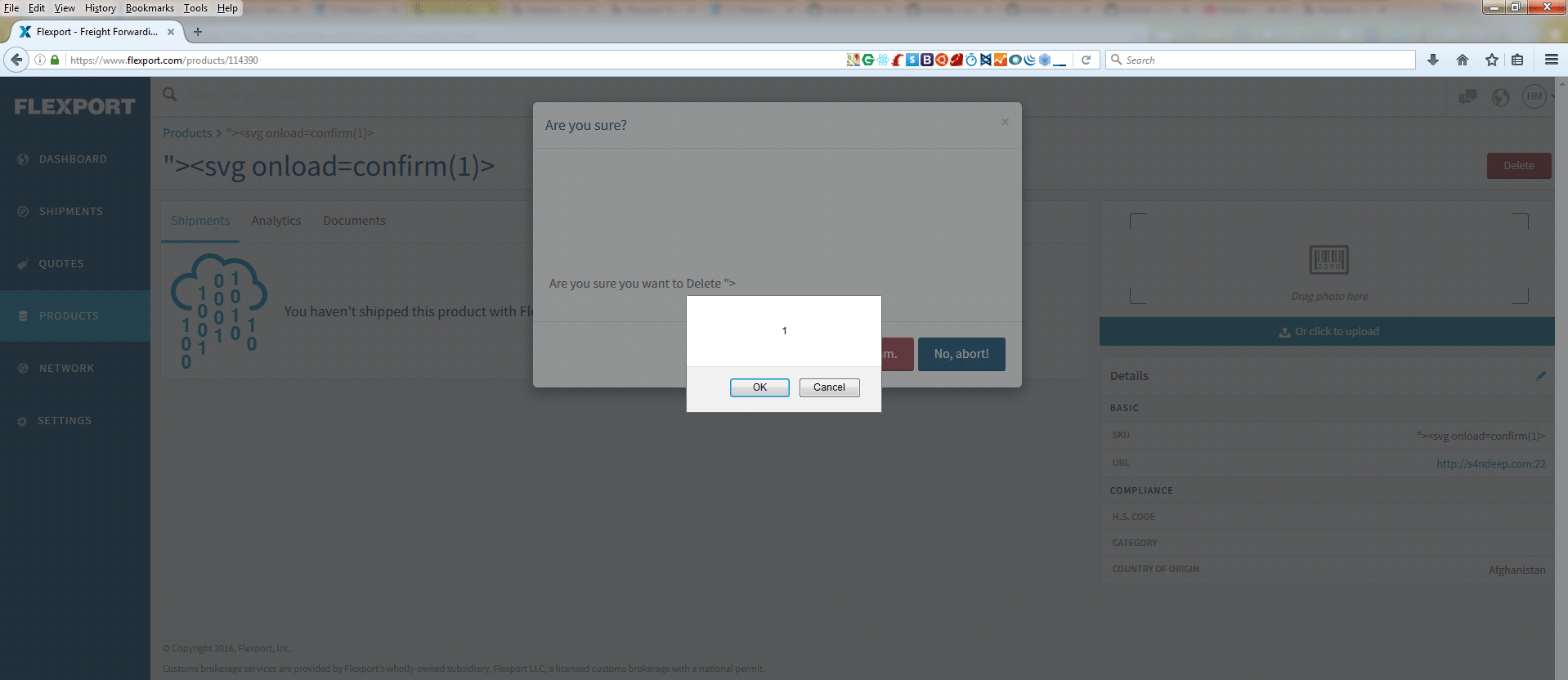
'Curiosity killed the cat'. I thought lets look at Infooby's web application for quick XSSing because in the program announcement (now gone and no more available), they're interested in having XSS reports. Initially, I have no idea that Infooby're acting maliciously and these guys have announced the program only to have the reports so that they can fix it and improve their web application. They wanted to have a win situation but only for them. One aspect of bug bounty program's announcement is marketing stunt or getting a media attention. I think Infooby wants limelight.
In a matter of few minutes, I found 2 XSS issues in their web application and reported these (#130596 & #130733) via Hackerone. One of the XSS is still live. Open the following URL in Firefox browser.
The screen-shot is also given below. The other XSS was here (now I think they fixed it): https://infooby.com/places?address='><img src=x onerror=prompt(1);>.
I found 2 XSSes in quick time so I thought there're many more and I wanted to continue testing but soon started getting the error message i.e., 'Resource limit is reached' and/or 508 status code and/or even site was getting down again and again. It shows that Infooby is not fully prepared for the initial onslaught from the HackerOne's community. The homework from Infooby's side was missing because if you will announce the bug bounty program, there is a great chance that several people will immediately start scanning your web application with the help of automation tools (may be as a part of initial and quick probe). The automation tools mean bombardment of attack payloads. The other testers have also noticed the error message and in the meantime, Infooby awarded someone a 20$ bounty but in the program announcement, they had mentioned the minimum bounty amount will be 50$. Meanwhile the Infooby's main site was going down and up again and again because of ongoing testing from the community.
On the next day, I received an email from HackerOne regarding the status of Infooby's bug bounty program. In short, it was no longer there. The contents of the email can be seen in the screen-shot.
It raises the following questions in my mind and still there are no clear answers. How can we stop this type of thing or fake/questionable bounty program in the future? What mediators or facilitators like HackerOne and BugCrowd can do in this regard? What happened to the bug reports (current status is 'Not Applicable') Infooby had received in the meantime and Isn't they will fix bugs for free?
I think we can not stop announcement of fake bug bounty program(s) given if it is announced on the company's own web page. Any web site can do this and no one from outside can ask a question about its credibility given it is the company's sole jurisdiction. The bug bounty mediation/facilitator platforms like HackerOne and BugCrowd still can do something like e.g., 'security deposit for guarantee or best practices'. The idea is same as we see in real life e.g., if we rent a house or apartment, we used to pay some deposit and at the time of leaving the house, we normally get the money back. HackerOne and BugCrowd should ask for this deposit money in order to make sure that company is serious in bug bounty program and if in case company does some questionable practices, HackerOne and BugCrowd may take the money from this deposit or pool and distribute it to the valid bug submitters. If there will be a pool of money like that (e.g., initially it can be a pool of 5K USD per bug bounty program announcement) than there will be no more free bugs even if the bug bounty program is gone or vanish. This pool of money will motivate both parties to work in a best possible way.
Now a days, in general, we (i.e., bug submitters) participate in a bug bounty program like a race. We try to find bugs (especially low hanging fruits) as soon as possible, immediately after the program announcement, without keeping an eye on how genuine a bounty program is. I think this is the wrong approach at the moment (unless we have a deposit or pool as I mentioned earlier) given we do not know in start how reputable a program is. Believe me, the bugs are there and it is not necessarily to treat it like a race. Trust in your capabilities and you will find bugs given you will have enough motivation. Happy Hunting.
Note: If you guys have any other good idea on how can we stop fake program(s) or wants to share your bad experience(s) with the bug bounty program(s), please feel free to comment.
